Microsoft Azure platform offers vast number of services and solutions, offering massive possibilities to solve business problems combining various Azure services and products. Microsoft cloud computing platform are likely to be less expensive and more flexible, more reliable, and more secure than on-premises servers and solutions.
Security is a key focus of Microsoft Azure who invests enormous amounts of money into securing its infrastructure – more than 1 billion USD (yes, that is 1,000 millions of USD) of investment in security, research, development, and cyber security experts annually. With such an enormous amount of investment in security, there are few companies that can afford financial resources, expertise, and infrastructure at such a large scale.
Microsoft knows that telling everyone how large investments have been made or which latest-and-greatest state-of-the-art security technologies have been implemented is not enough to win customers. That is why Microsoft recognized the importance of conforming to global privacy and compliancy standards across regulated industries and markets globally. Microsoft offers the broadest and the deepest set of compliance offerings of any cloud service provider.
Many industries have recognized the high compliance and security standards that Microsoft Azure provides to their customers, which is an extremely crucial element in the trust relationship. Having the possibility to choose from so many products and services, customers sometimes have difficulties choosing the right product or service and object that going “to the cloud” might not always be the easy path. While it is impossible to single out a product or a service unique for an industry, there are some products and services that are more attractive to an industry.
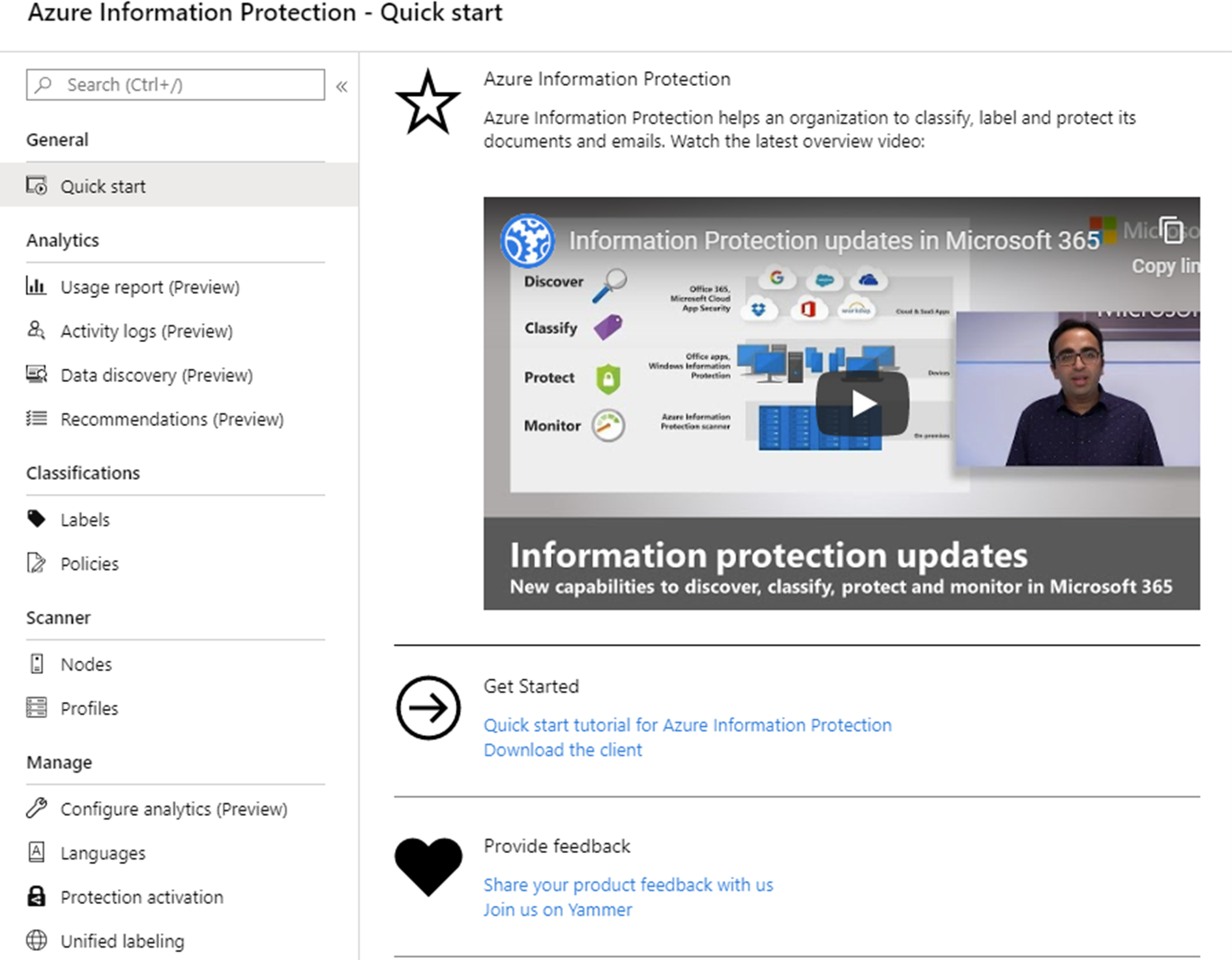
Financial institutions such as banking and insurance companies work with sensitive, personal and business financial customer data that must be secure. Moreover, the large number of various documents differ in sensitivity and privacy nature which is an additional burden to personnel. Manually selecting and classifying large volume of files, emails and different type of data according to its sensitivity and privacy characteristics is not easy as the classification needs to be unified and fast. Microsoft Azure Information Protection, or sometimes abbreviated as AIP, is a cloud-based solution that solves the problem of manual classification and protection of sensitive data and applies the classification labels and protection to data automatically, unobtrusively and quickly. Implementing Azure Information Protection can help employees so they can focus on their primary tasks while sensitive data is protected while they work.
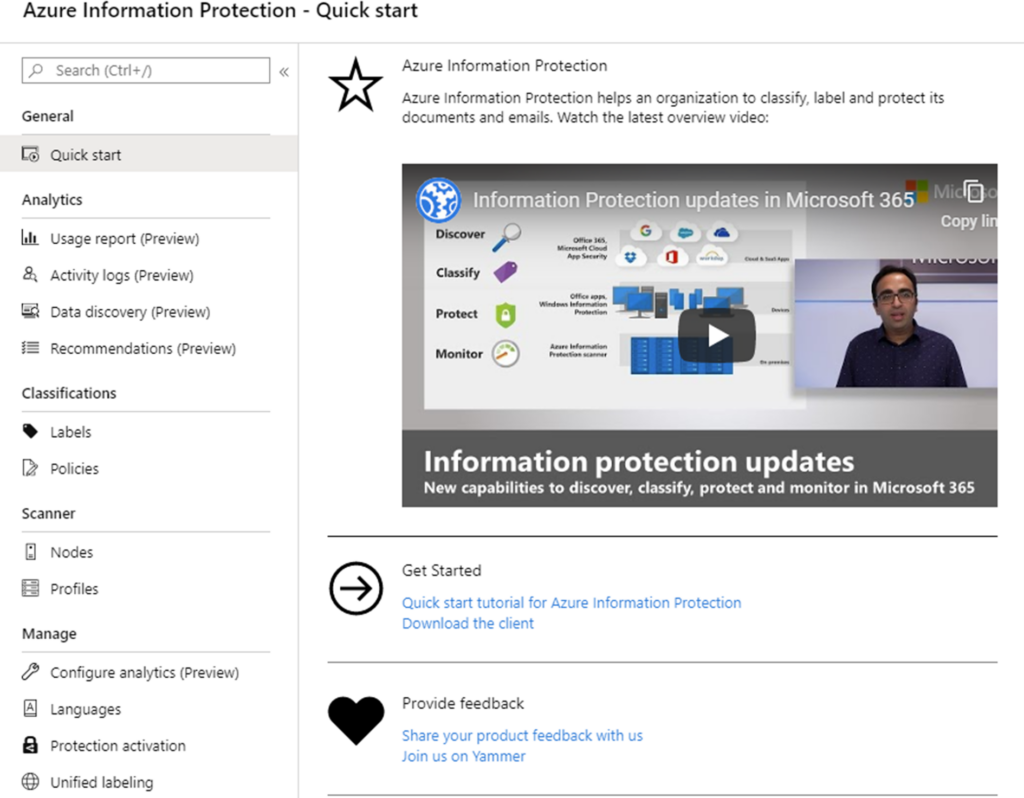
Implementing Azure Information Protection is beneficiary in many aspects, especially if a company implemented General Data Protection Regulation (GDPR) processes, they could become more efficient and cost-effective, while Data Loss Prevention (DLP) policies can achieve better data classification results.
The benefits of automating classification and protection using AIP are obvious during all phases of data information protection lifecycle. Sensitive documents across a range of locations can be discovered faster, based on the rules you define. Classification and labelling of sensitive data can be done more efficiently and automatically, while keeping possibility for manual intervention as well. Applying flexible protection actions, such as restricting access and encryption is welcome as it helps cover different protection levels. Azure Information Protection offers monitoring over protected data enabling you to gain insight into how the data is distributed, consumed and to take remediation steps if necessary.
Companies do not have to be fully cloud-based to implement Azure Information Protection. Customer data can be managed fully in the cloud, but many organizations have not yet moved entirely to the cloud, but still have data stored on-premises, while others are yet to begin their cloud transformation and keep their data on-premises completely.
Organizations that have data on-premises can take advantage of Microsoft AIP deploying Azure Information Protection Scanner to discover data against their on-premises repositories, like file shares and SharePoint libraries.
Microsoft Azure Information Protection, as many Microsoft technologies are, can be spotted in other Microsoft products, which brings us to a product that can be attractive to public, governmental bodies and institutions and non-governmental organizations, or NGOs, as well.
These governmental and non-governmental organizations also work with sensitive data that must be protected. Very often, employees work late and after hours and, in many cases, carry sensitive documents outside protected, on-premises environment. Furthermore, employees use a variety of operating systems, cloud-based repositories and online storage locations, access organizational resources from distinct locations and countries. These environments do not have unified security standards and levels and what is even more critical, when outside organizational boundaries, it is exceptionally difficult to control distribution and dissemination of organizational data and how employees treat sensitive data.
Microsoft Cloud App Security can help address these problems and moany more as well. To quote Wikipedia, “Shadow IT, also known as Stealth IT or Client IT or Fake IT, are Information technology (IT) systems built and used within organizations without explicit organizational approval, for example, systems specified and deployed by departments other than the IT department.
Examples of these unofficial data flows include USB flash drives or other portable data storage devices, MSN Messenger or other online messaging software, Gmail or other online e-mail services, Google Docs or other online document sharing and Skype or other online VOIP software—and other less straightforward products: self-developed Access databases and self-developed Excel spreadsheets and macros. Security risks arise when data or applications move outside protected systems, networks, physical location, or security domains.” (https://en.wikipedia.org/wiki/Shadow_IT)
I would like to emphasize the last sentence: “Security risks arise when data or applications move outside protected systems, networks, physical location, or security domains.” According to studies, Shadow IT makes up more than 65% of cloud services introducing unknown and unmanaged risks into the environment. Cloud App Security can help you identify which cloud applications and services are being used across your organization. You can get an insight whether these cloud services are approved for use, are being accessed beyond trusted organizational environment and whether are managed or unmanaged by IT organizational department.
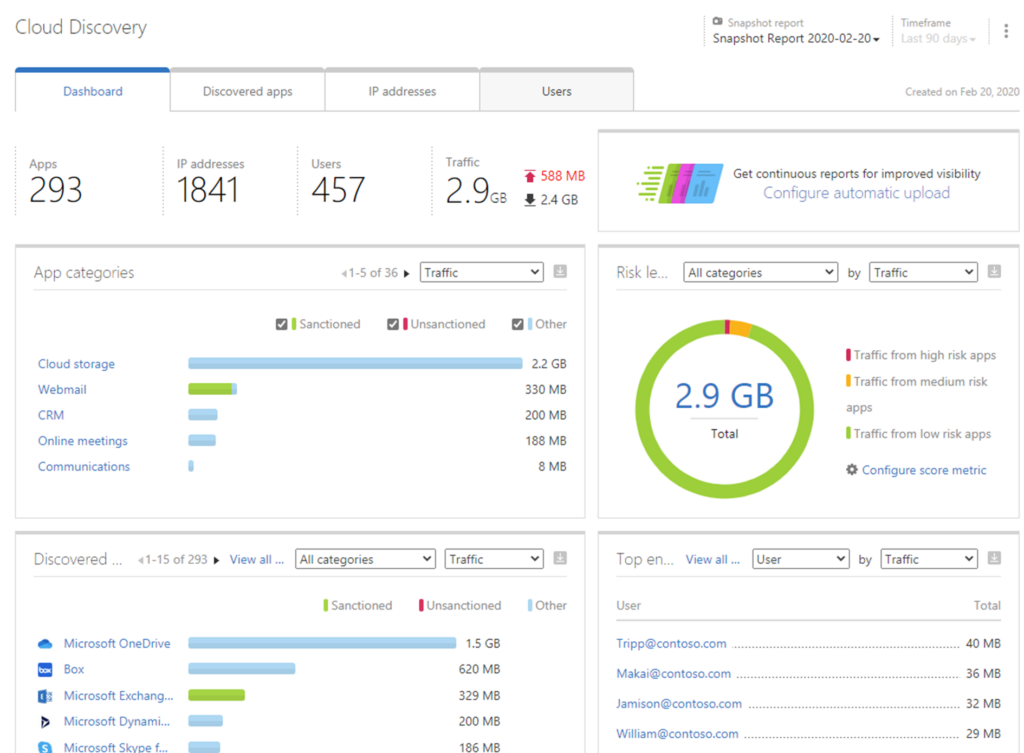
It is important to be sure whether all applications employees use meet security policies and standards set by internal IT department and relevant compliance or industry requirements. Using Cloud App Security, you can assess compliance and risk of discovered cloud applications against more than 70 risk factors and allow IT department to make informed decisions and actions about which applications or cloud services should employees be able to use or blocked entirely. You can then set up policies to detect changes in user behaviour, usage pattern of cloud services and applications, and set alerts to be notified when these behavioural anomalies happen, such as mass download, unusual usage pattern, time or many other data and information exfiltration attempts.
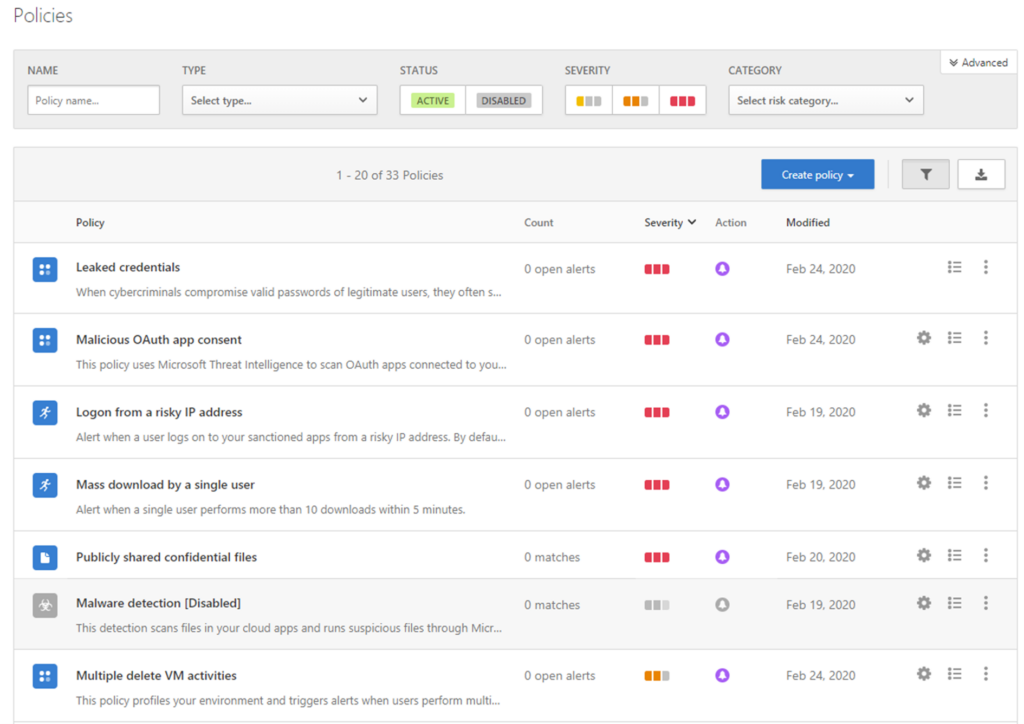
Additionally, Cloud App Security (or CAS) incorporate tight integration with other Microsoft technologies, like Azure Information Protection. Data Protection Policies (or DLP) can be enforced more efficiently as you can use CAS to identify files that contain sensitive information and provide immediate remediation actions including encrypting files, removing external sharing permissions, or placing files in quarantine. Also, you can impose scanning of files as soon as it is uploaded to a cloud application and automatically apply labels and relevant encryption or restrictions.
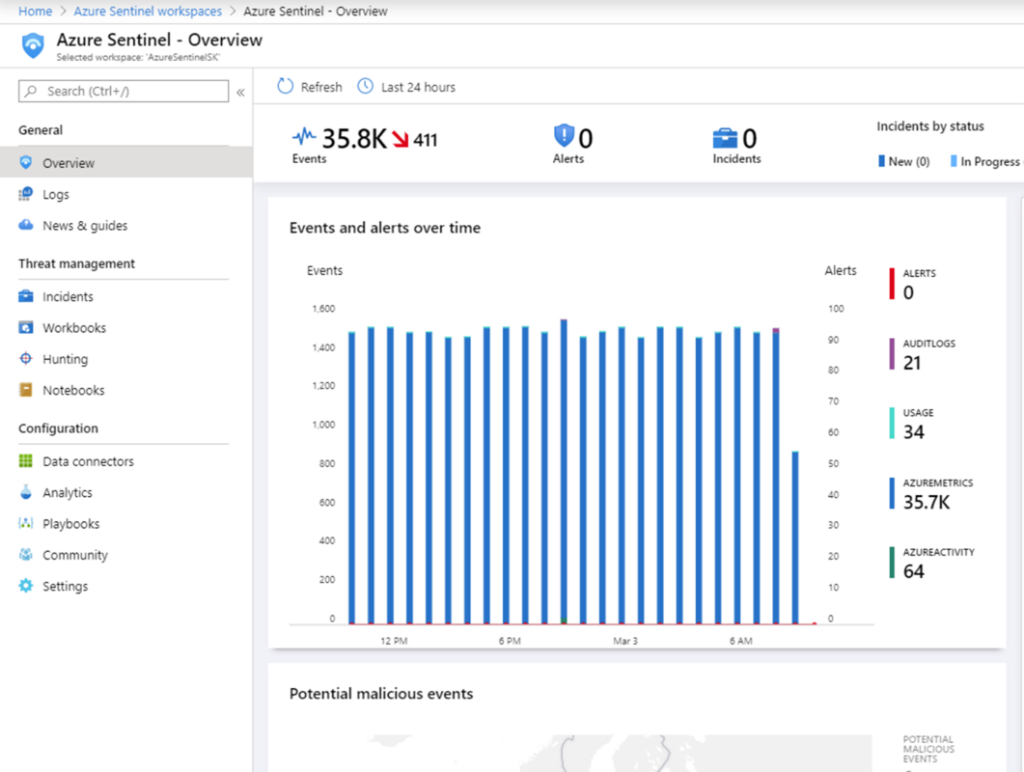
Being a Cloud Security Expert makes me more familiar with related industries than others, but that does imply by any means that these recommendations and products are not relevant to other industries. Recent studies show an increase of threats to software and hardware manufacturers, and this is where Azure Sentinel helped a company where I was engaged as a Cloud Security Consultant. Being one of the biggest software development companies, this company had most of their workloads moved to Azure, but their security posture was not yet at adequate levels. Azure Sentinel was a solution to their growing Azure infrastructure and as a built-in security information event management (SIEM) and security orchestration automated response (SOAR) solution was a perfect match. It is a cloud-based threat intelligence and security analytics solution suited not only for your cloud-based workloads and products but to entire enterprise as well. It collects data across all organization, users, applications, devices and investigates threats powered with artificial intelligence, empowering you to respond more rapidly, reducing the chance for data loss.
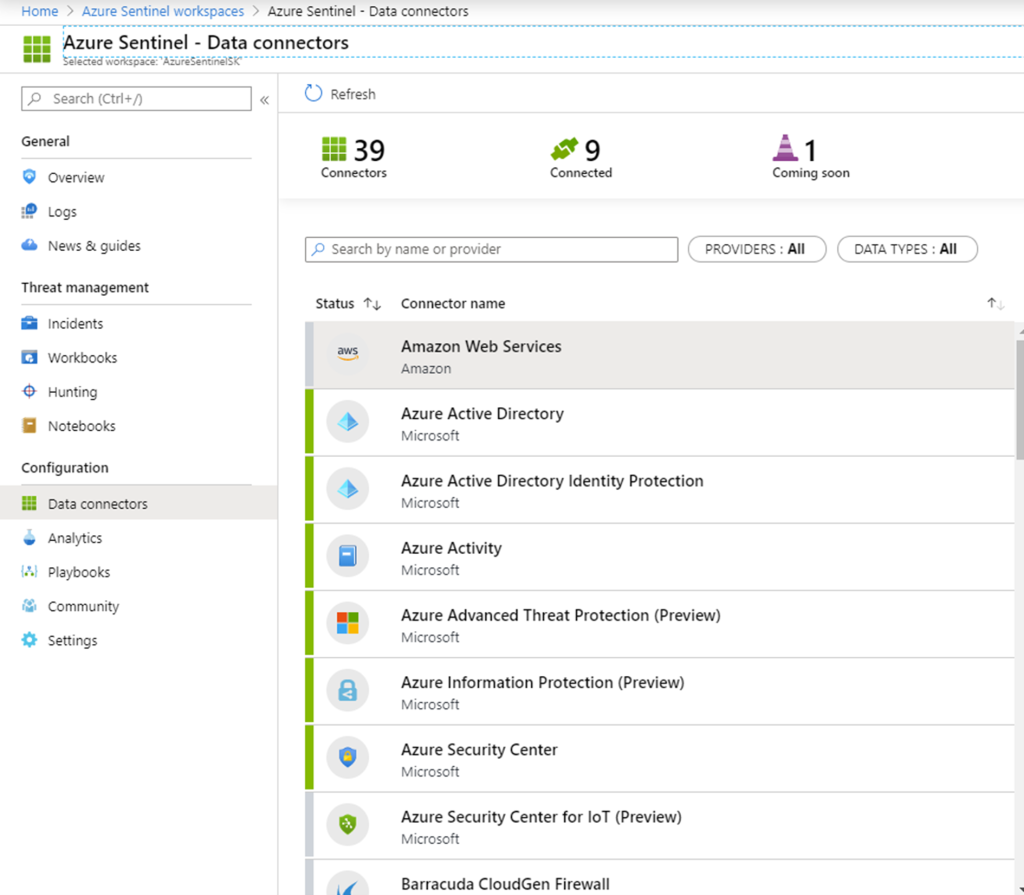
To be able to analyse data, you first need to connect to your data resources through connectors. Azure Sentinel includes many connectors for Microsoft and third-party solutions, including Office 365, Azure Active Directory, Microsoft Cloud App Security, Amazon Web Services, and more. To onboard non-Microsoft solutions, you can use common even format, Syslog or REST-API.
Azure Sentinel also features strong search and query hunting tool, based on MITRE framework. MITRE ATT&CK™ is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. To provide an insight into attacks, you can create custom detection rules based on queries, using KQL, or Kusto Query Language.
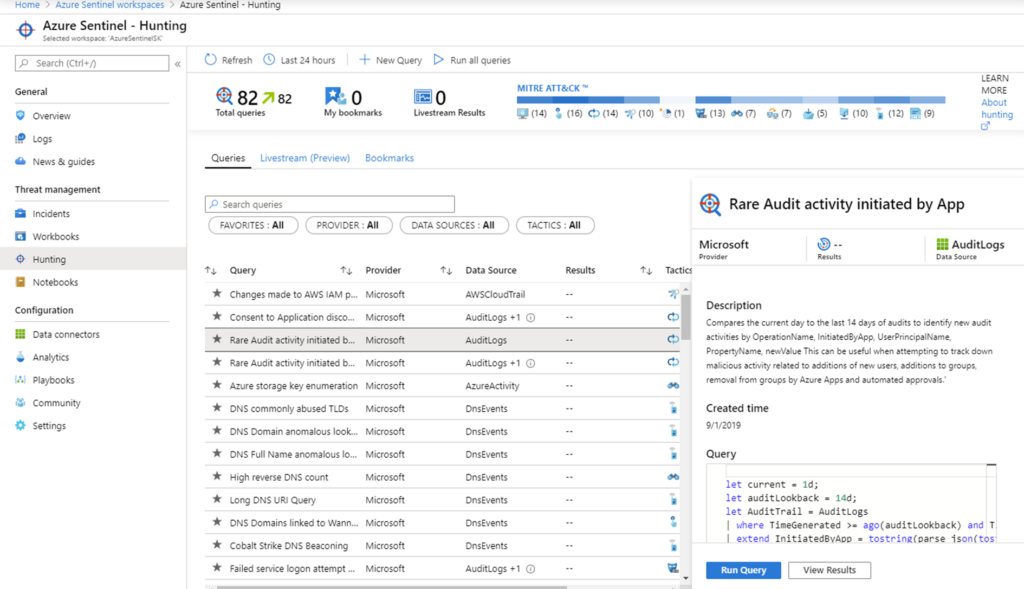
Finally, you have been introduced to three powerful and comprehensive cloud-based security products which are applicable and usable in any industry, organizational type, or size. Do not rely only on one Microsoft Azure technology or product – Microsoft Azure has many security products and features that can protect your organization or company at many levels.