We are already two weeks into year 2021 and the dust has not settled yet from last September 22-24, where we witnessed the first part of Microsoft Ignite conference as a fully digital event. There have been a lot of news and announcements made at the recent event and we already covered Azure Sentinel news in this article.
The second part of Microsoft Ignite is March 2-4, 2021. – similarly, it will be a digital event and I expect it to be, as its older sibling was, full of latest technical announcements not just from Microsoft, but from Microsoft’s partners as well.
As we anticipate the second part of one of the most important Microsoft conferences, let us look at some remarkably interesting enhancements in Azure Security Center revealed few months ago at the last event.
One of the biggest changes in Azure Security Center users immediately notice is its visual overhaul, needed to accommodate not only branding changes but because new functionality needed its place too.
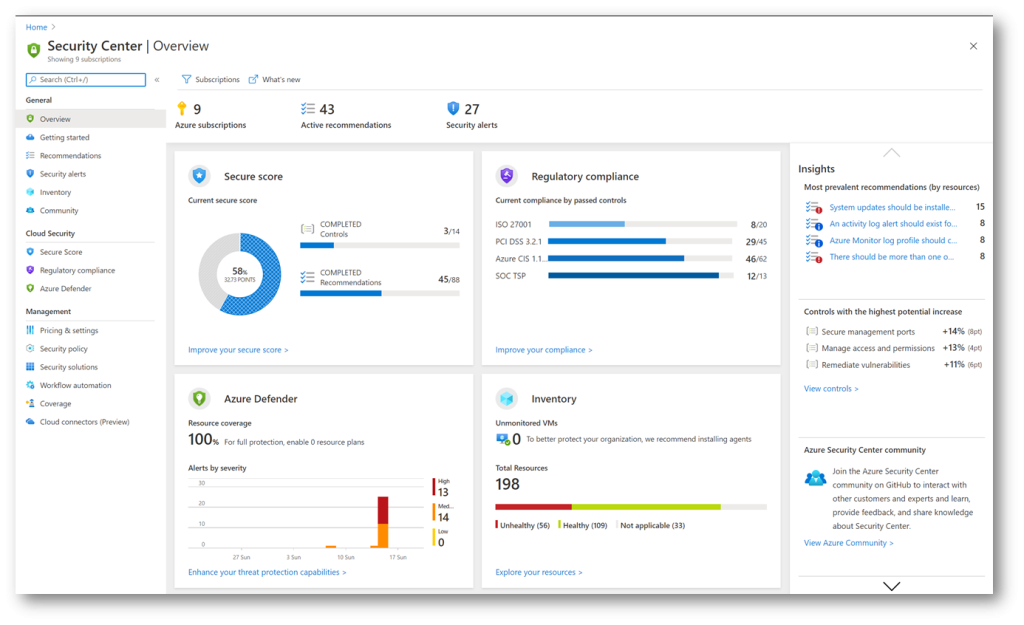
General, Cloud Security and Management are three distinct parts of newly redesigned menu blades, containing specialized blades for management, protection, and security insight posture.
General blade shows refreshed and better organized Overview dashboard and information, where each Cloud Security menu blades has its own dashboard, together with Inventory dashboard, too. Of course, each dashboard is still clickable, opening its respective pages instantly. Secure Score status is calculated based on simplified points and displayed as a percentage. The percentage-based score is present not only in Azure but in other products and features, like Compliance and Security in Microsoft 365, and it provides better understanding of a status and enables administrators to follow trends and compare statuses more easily.
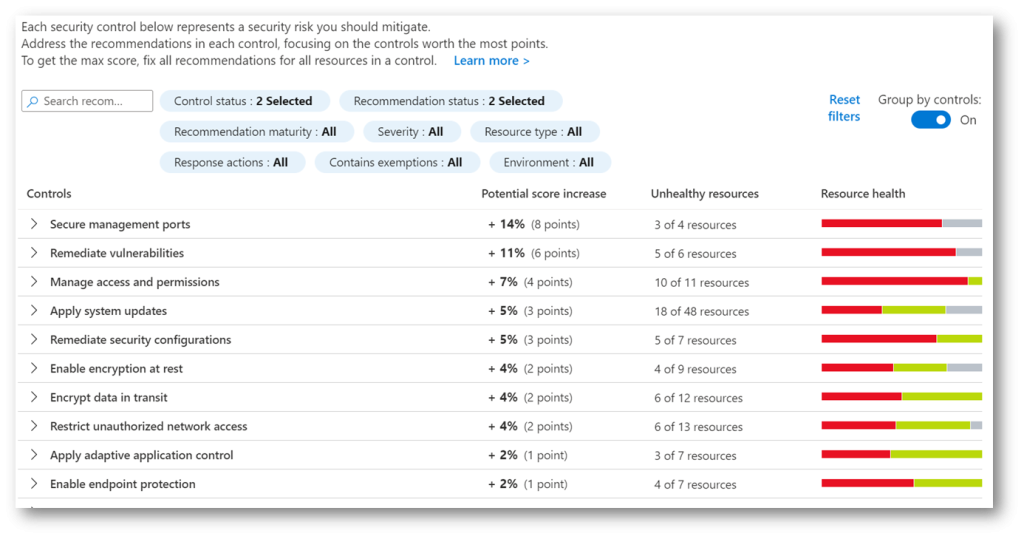
The other two dashboards that are placed on far right of the Overview page, reveal valuable information: Insights and Controls with the highest potential increase of the Secure score.
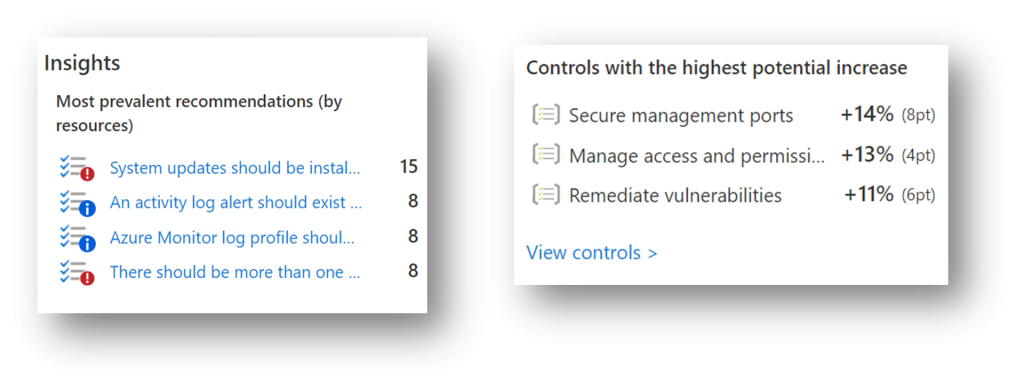
Insights dashboard shows most prevalent recommendations by resources, enabling you to identify the most frequent recommendations and their number, while Controls with the highest potential increase show you top security risks and potential score increase in points and percentage, in case all recommendations of a control group have been fixed.
The release of Azure Defender follows the product family branding and it covers a range of plans which cover a wide range of protection across service, data and compute layers of Azure environment:
- Azure Defender for App Service,
- sAzure Defender for Servers,
- Azure Defender Storage,
- Azure Defender for Key Vault,
- Azure Defender for DNS,
- Azure Defender for Resource Manager,
- Azure Defender for SQL,
- Azure Defender for Kubernetes and
- Azure Defender for container registries.
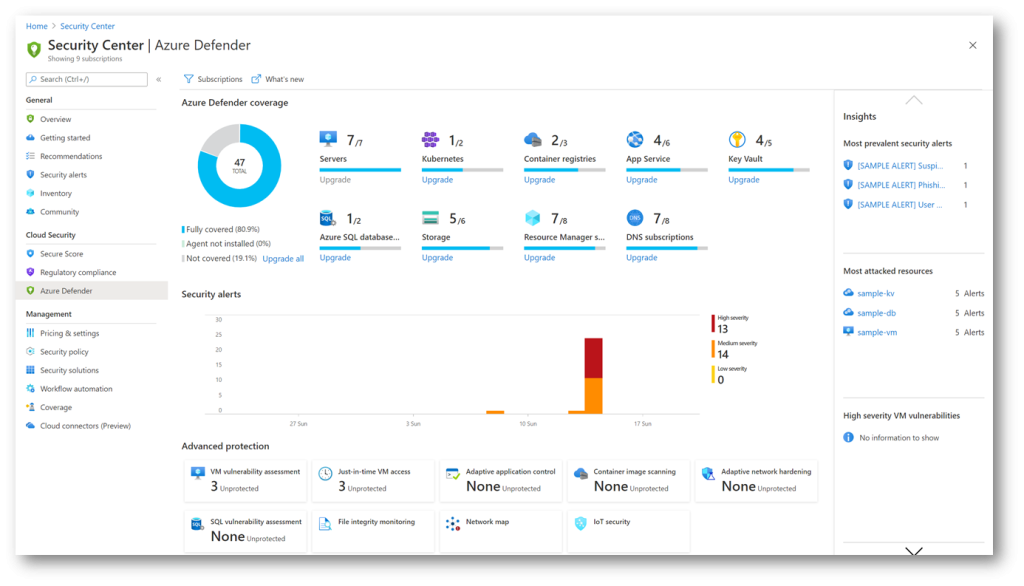
Now, introduced security settings are available across services in the Security group, under Security blade.
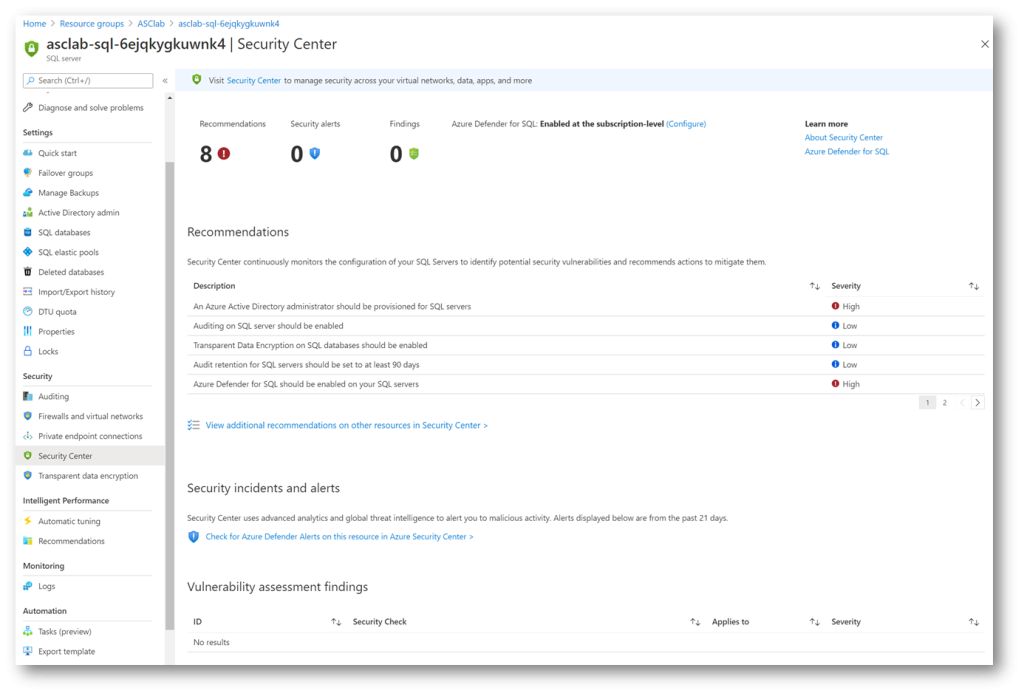
Services which recommendations are shown in Azure Security Center have similar experience and content, they share common color coding for quick identification, categorization and triaging of events, present since the birth of Azure Security Center. Recommendations, Security Alerts and Findings display number of events at the top, with additional Recommendation descriptions in the middle, with the inevitable and welcome link to ASC Recommendations blade. At the bottom, Vulnerability assessment findings shows security check findings and their respective severity level. While in Recommendations, for an easier item identification and assessment, you have the option to group recommendations by controls, or leave it ungrouped, showing the most critical fixes at the top.
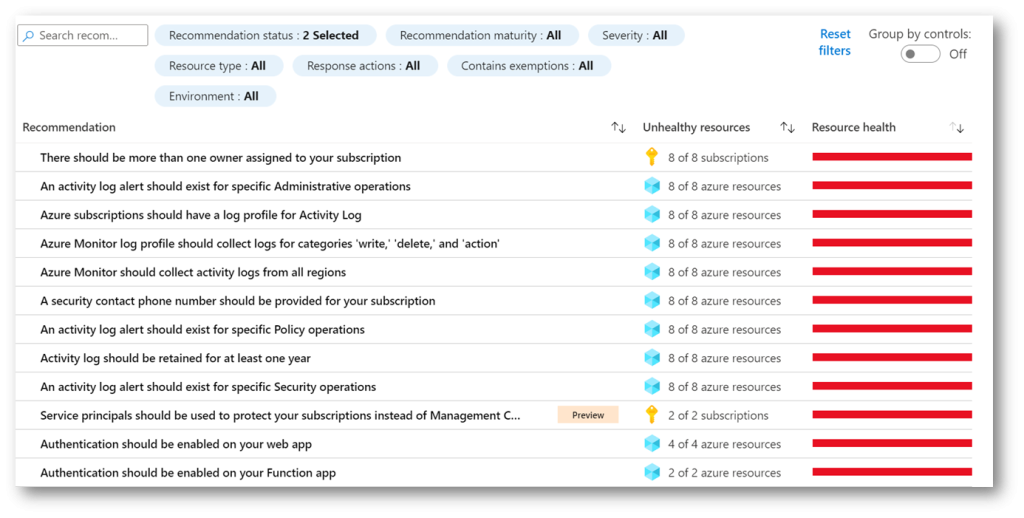
One of the requested functionalities in Azure Security Center was an option to create an exemption from recommendations and from Secure Score for a specific resource. In the special situation where you have a resource that does not need to be listed as unhealthy, and to prevent a negative score impact, we can now exclude such a resource from being observed.
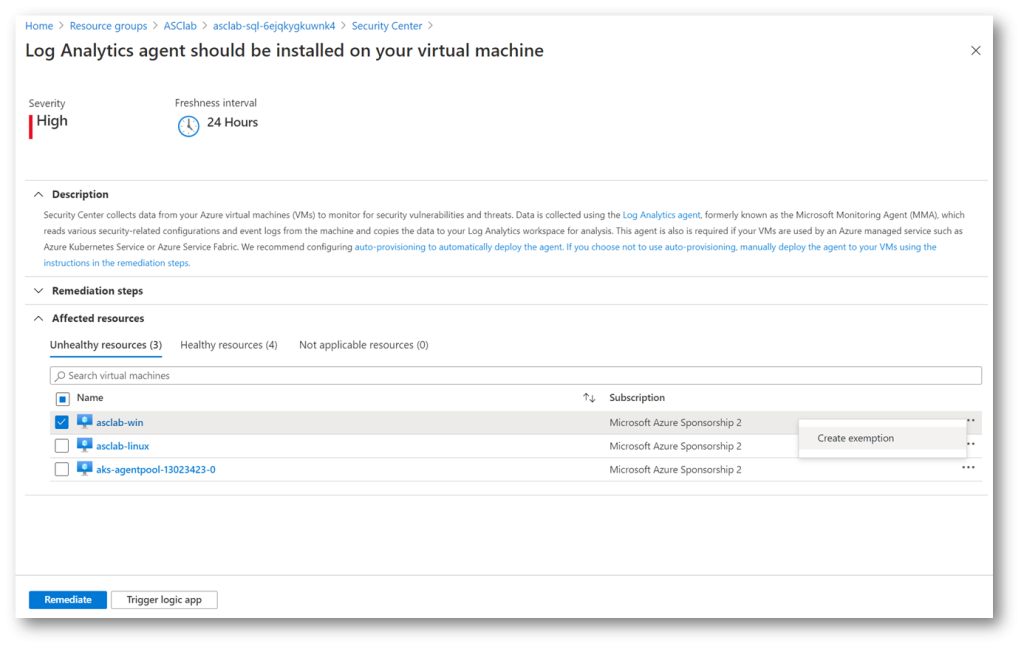
Now, the Create Exemption feature is still in preview phase and its scarce options might change in the future. You can set an expiration date and select one of the two exemption categories, resolve and exemption through a 3rd party or, accept the risk of exempting a recommendation.
Either way, ensure that by exempting a resource from being shown in ASC recommendations you do not lower or otherwise negatively impact security posture of your Azure environment.
Azure Security Center enhancements include multi-cloud security position management with the help of Azure Arc and, after connecting, Azure Security Center can show recommendations from Amazon Web Services (AWS) and Google Cloud Platform (GCP) clouds as well.
Connecting AWS account to Azure Security Center should not be more complicated than creating a simple virtual machine in Azure. Here are the high-level steps to connect an Amazon Web Services account:
- In the AWS Console, click Services, and below Security, Identity and Compliance select IAM.
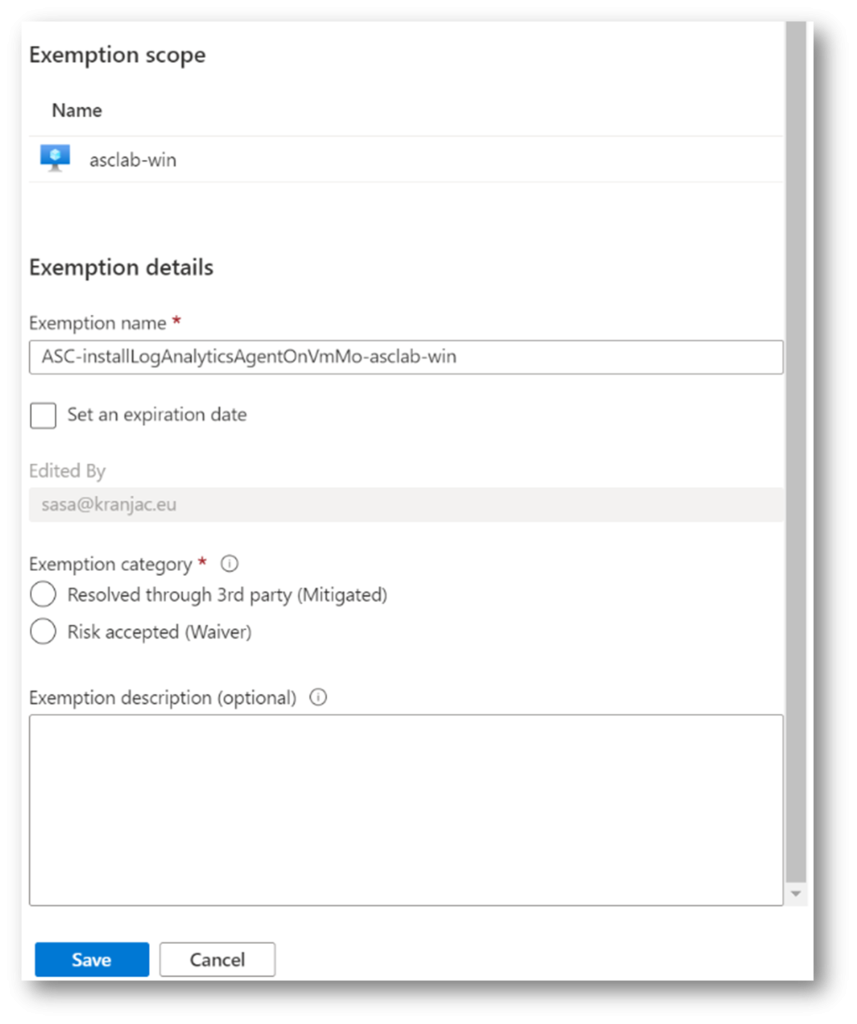
- Under Role, create Another AWS Account, and enter Microsoft’s Account ID (158177204117).
Check Require External ID and enter External ID, an identifier value unique to you (that is, your Azure Subscription ID). Click Next: Permissions. - Add permissions for the role: SecurityAudit, AmazonSSMAutomationRole, and AWSSecurityHubReadOnlyAccess
- Optionally add tags and complete the task. On the Summary page, copy the Role ARN (Amazon Resource Name), as you will need it in ASC wizard.
- In the Azure Security Center, in the Management group, click Cloud Connectors (Preview) and then click Add AWS account.
- Complete Basics and select Assume role authentication method. The other way to authenticate ASC to AWS would be to create a user in AWS and enter its credentials (Access key ID and Secret access key, obtained on the Summary page in AWS Console). In AWS role ARN field, paste Role ARN. Click Next.
- Create a Service Principal by using provided PowerShell script, or manually. Enter Service Principal client ID and secret and click Next.
- On Review and generate page, complete the wizard.
After you complete the Connect AWS account procedure, do not be surprised if there are no AWS entries – it could take several hours before you can see AWS Recommendations in Azure Security Center. Similar steps are needed to connect a GCP account – after that, you can work with AWS and GCP recommendations in the same way as you do with “domestic” ones, that is, with Azure recommendations.
Other notable announcements include ability to continuously export recommendations and alerts in real time to Azure Event Hubs, Azure Monitor and Log Analytics Workspaces, providing capability for integration with Azure Sentinel, Power BI and other solutions.
Azure Security Center can send emails notifications about alerts for all severity levels, recommendations now include severity indicator and freshness interval, while preview recommendations now are not included in Secure score anymore.
Planned changes to Azure Security Center include Enhancements to SQL data classification recommendation and new recommendations to increase coverage of Azure Security Benchmark. With little less than two months to go, we are anticipating the second part of Microsoft Ignite conference in March, where we expect new announcements, feature introductions and enhancements, and possibly some new, exciting products.