Azure Sentinel is Microsoft’s recent addition to a hybrid cloud security landscape – it is designed to provide cloud-enabled intelligent analytics not only of your Azure resources, but of on-premises and other cloud resources such as Office 365 and Amazon Web Services as well.
Azure Sentinel is Security Information Event Management (SIEM) and Security Orchestration Automated Response (SOAR) product, and I hear you say “Oh, no, not another SIEM product”, but unlike other on-premises solutions, Azure Sentinel has a lot of horsepower under the hood. It does not require complex installation, or time-consuming infrastructure setup as it is completely cloud-based, powered with artificial intelligence and scaling capabilities. Azure Sentinel is a hybrid cloud security solution, capable of processing and analysing data from Azure and other cloud provider services, as well as from Windows and Linux workloads no matter where they are, on-premises or in a cloud. Moreover, it can analyse data from third-party security solutions but also data coming from Office 365, Cloud App Security, Azure Information Protection and others.
The enormous quantity of data hybrid resources generate, requires a lot of computing power to analyse, to get useful and actionable information out of it. Azure Sentinel helps and provides capability in four crucial areas or stages:
- Collect. Collecting data from multiple sources and clouds, on-premises, applications, infrastructure, users, services and others.
- Detect. Detect threats to protected and monitored resources as they happen, minimising the time to react to threats.
- Investigate. Powered with artificial intelligence, search for and discover malicious activities across all protected assets.
- Respond. Once a threat is known, avoid manual actions and respond to threats with automating tasks.
As of its public appearance, at the end of February, Azure Sentinel is in Preview and not all its features are yet fully available. Pricing is still unknown too which will be announced before leaving the Preview phase.
Meanwhile, why not try Azure Sentinel? There are some prerequisites though. You need to have a contributor permission to the subscription and a Log Analytics workspace. Currently, Azure Sentinel supports workspaces created in the following regions only: Australia Southeast, Canada Central, Central India, East US, East US 2 EUAP (Canary), Japan East, Southeast Asia, UK South, West Europe and West US 2. Support for other workspaces might be available later.
Before anything else, you need to enable Azure Sentinel.
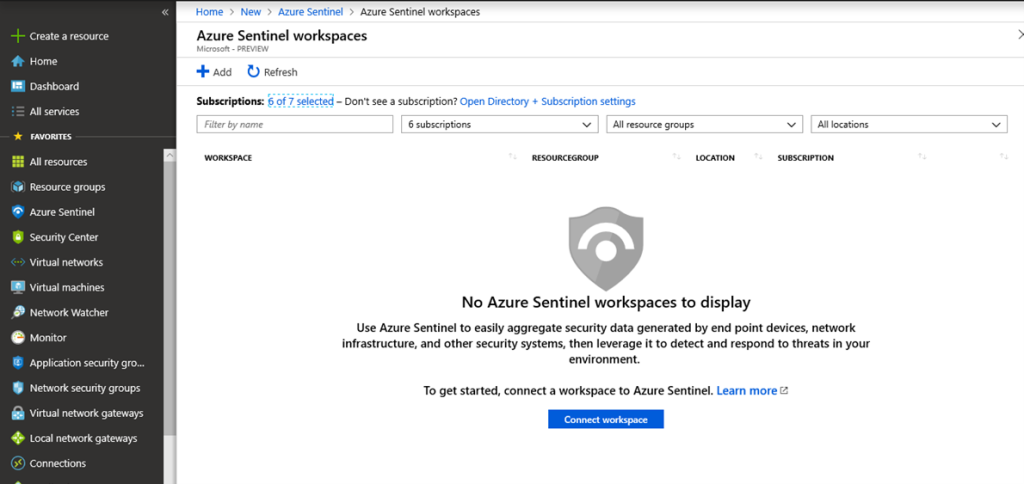
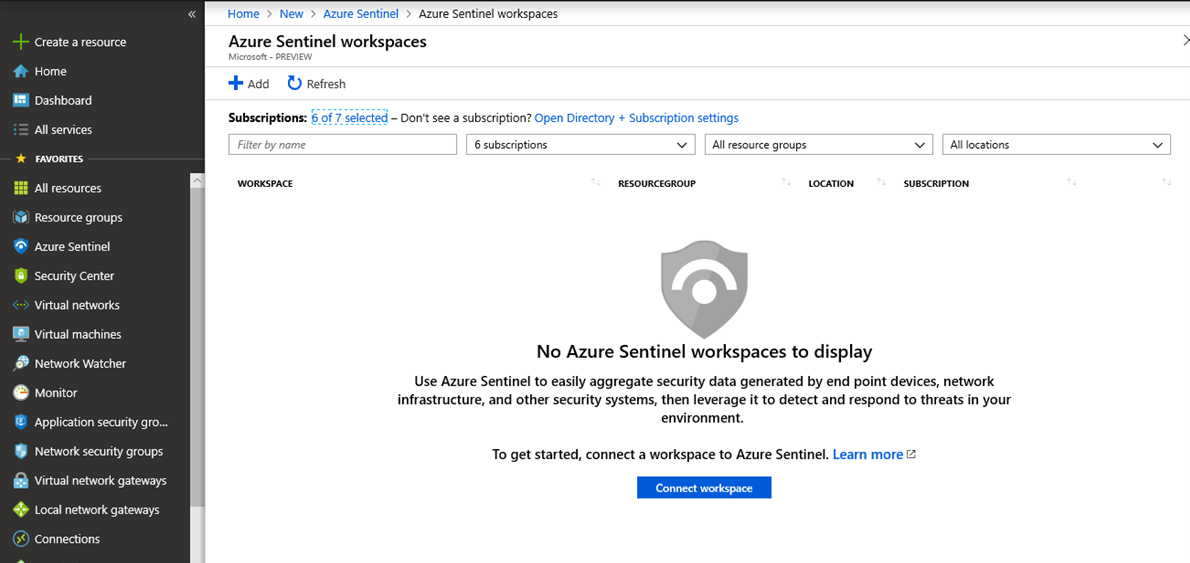
- Either go to Marketplace, All Services or search for Azure Sentinel in the search field. Click on Azure Sentinel and click +Add
- Choose a workspace to connect to Azure Sentinel. The workspace needs to be created in one of the supported regions. Click Add Azure Sentinel.
After you connect a workspace, you need to connect data resources to Azure Sentinel to be able to forward log events and data for analysis. Click Data Connectors and a list of available connectors appears, enabling you to connect various data sources, from Azure Active Directory and Office 365 to third-party solution providers like Cisco ASA, Fortinet, Barracuda, F5 along with any publisher supporting Common Event Format (CEF) logs.

I wish the Data Connectors blade is formatted more clearer, for example as a list, or at least that the current tiled layout reveals what is configured and what is not configured yet. Remember, it is in a Preview and a lot of things can change here in the future.
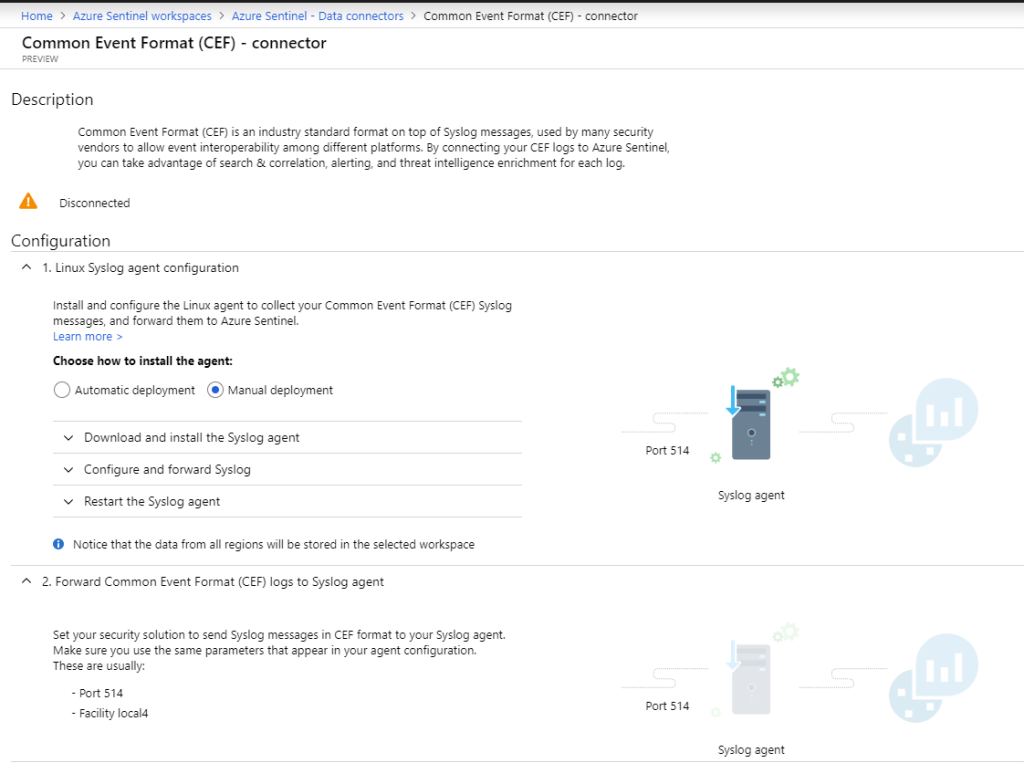
To configure a connector or a data source, click Configure and a new blade opens. Each connector has its specific settings, and depending on the connector, there is one or more steps required to connect a data source. The following image shows a Common Event Format (CEF) Connector and its configuration steps.
Some connectors do not require more than one click to connect such as Azure Active Directory Identity Protection connector and might have additional requirements, such as Azure Active Directory Premium P1/P2 license in this example.
Once you have connected and configured all required data sources, Azure Sentinel starts to collect data and it might take few minutes before you can see any activity. The more time passes, the more data Azure Sentinel has, and events and alerts numbers will go up and graphs will start to show up.
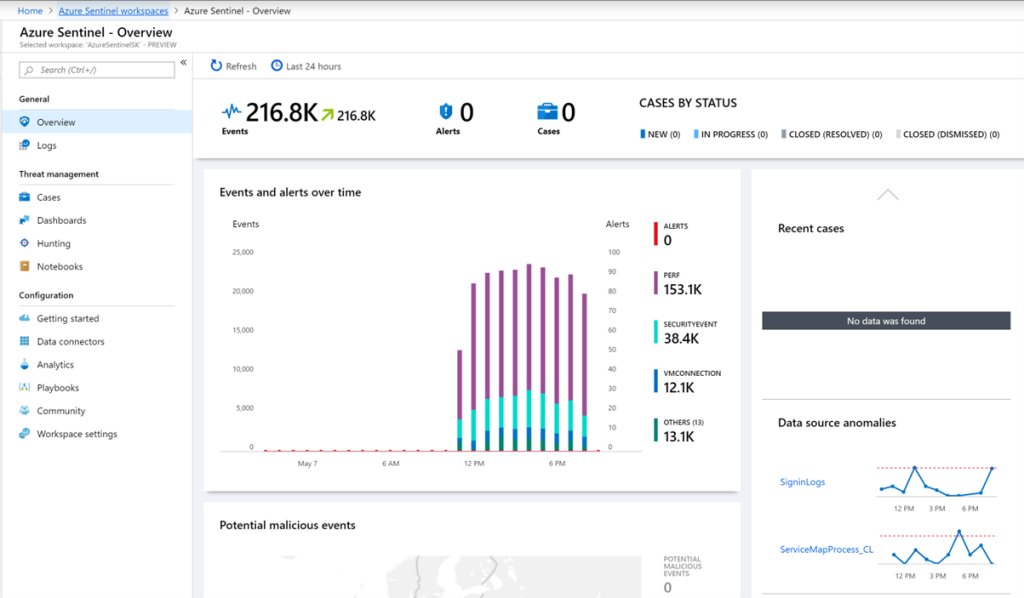
The Threat Management and Configuration options are on the left, while the central part is reserved for Events, Alerts and Cases quick overview, the graph representing Events and alerts over time and a world map displaying the source and location of potential malicious events.
The Log Analytics is directly accessible within Azure Sentinel via Logs blade and gives the possibility to use the well-known Kusto Query Language (KQL) directly on the Log Analytics Workspace connected to Azure Sentinel.
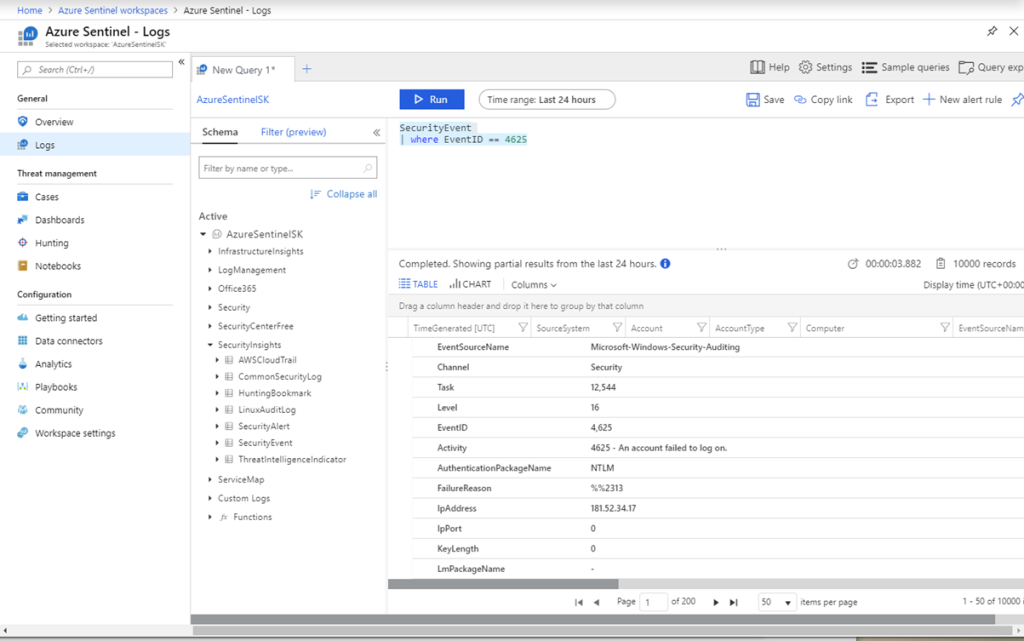
Here you can test and write your own log queries that you can use later in Analytics, to create custom Alert Rules. As an example, the following query will search for the Security Event ID number 4,625, which is an activity of an account failed to log in onto a Windows Virtual Machine.
SecurityEvent | where EventID == 4625
To create a custom alert rule in Analytics using the same query go to Analytics blade and click +Add.
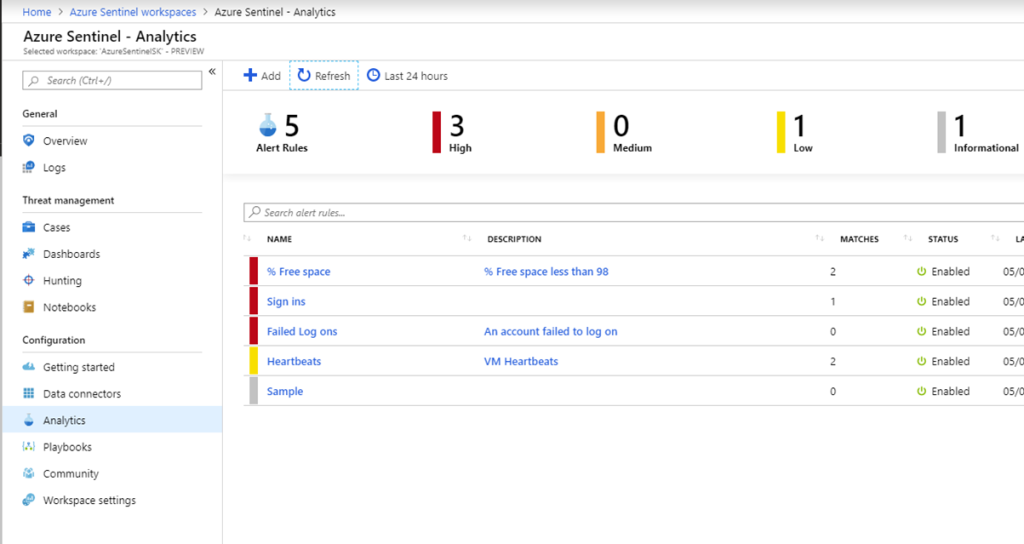
Enter a rule name, description, its Status (Enabled or Disabled) and choose Severity. The Logic pane will show the result graph once you enter the KQL query in Set alert query field. Click on a View query result logs > to immediately test the query in Log Analytics.
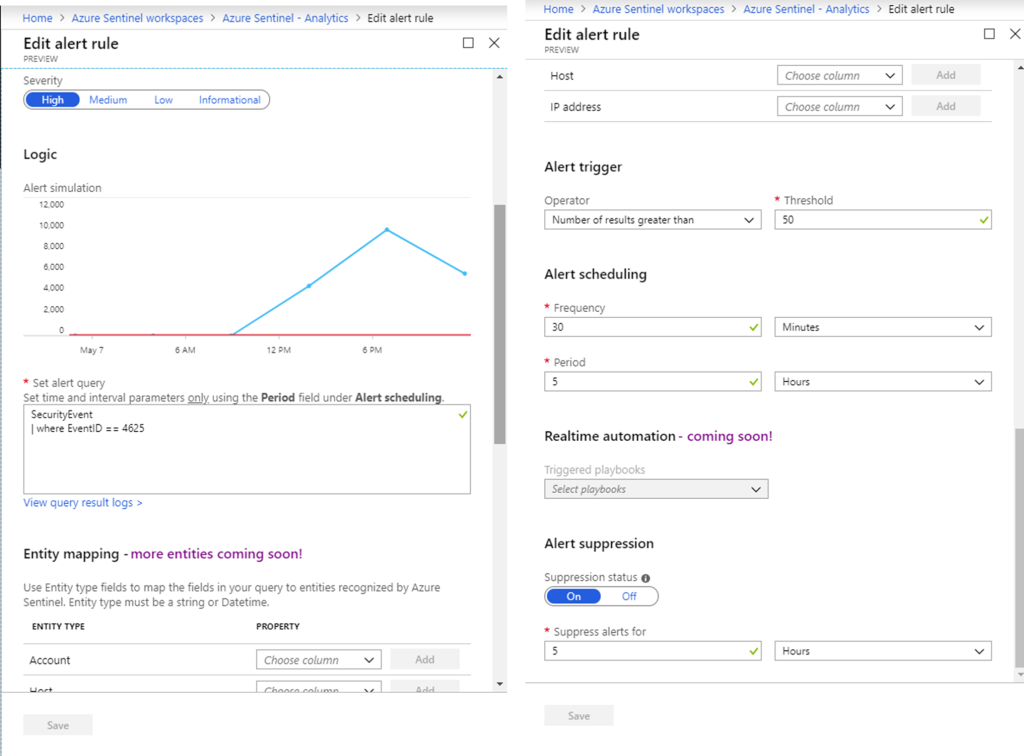
Set up an Alert trigger value as well as how frequently the alert will run. As the features are being added, real-time automation will enable instant alert triggering and more Entities will become available. After you click Save, a custom Alert will run according to the predefined schedule and generate alerts if a threshold of failed log in attempts has been reached.
You can add Playbooks, that is, define Logic App Workflows, that will automate actions based on alerts. You can define Playbooks that will perform various automated tasks, such as sending an email notifying you of increased number of unsuccessful log on attempts, blocking access to a virtual machine or shutting down a virtual machine, locking down a user account, blacklisting attackers’ IP addresses and many more.
An Azure Sentinel feature not immediately noticeable, and still under Preview, is Azure Sentinel Fusion. Fusion uses powerful algorithms and Machine Learning to analyse, triage and correlate events from multiple sources into security cases. Seemingly unrelated events might be connected, and Fusion helps us with the task. It is not enabled by default, and you can do it via Azure Cloud Shell, typing the following command:
az resource update --ids /subscriptions/{Subscription Guid}/resourceGroups/{Log analytics resource Group Name}/providers/Microsoft.OperationalInsights/workspaces/{Log analytics workspace Name}/providers/Microsoft.SecurityInsights/settings/Fusion --api-version 2019-01-01-preview --set properties.IsEnabled=true --subscription "{Subscription Guid}"
Azure Sentinel spans proactive, actionable security log analytics from cloud to on-premises environments, powered by the latest state-of-the-art Artificial Intelligence and Machine Learning capabilities. This is just a glimpse into Azure Sentinel features, and I can’t wait to try other recently announced features like detection’s authoring environment, ML algorithms in templates, code snippets, model management, model deployment, workflow scheduler, data versioning capabilities and specialized security analytics libraries and more.