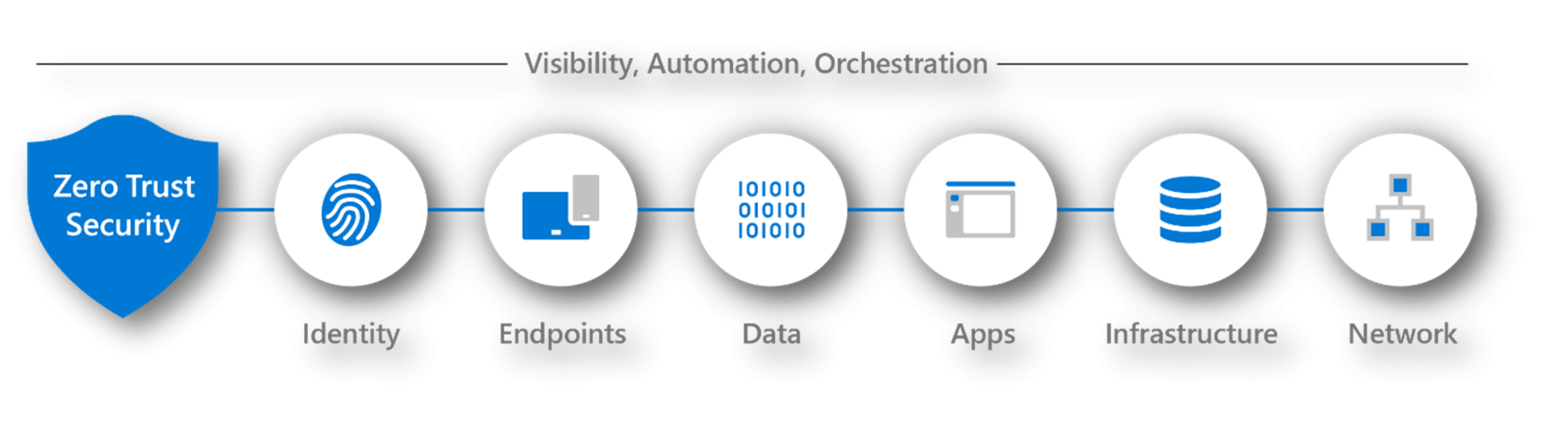
A new book: Mastering Microsoft 365 Security and Compliance
I am thrilled to announce my new book “Mastering Microsoft 365 Security and Compliance” is now available for preorder on Amazon!This would not be possible without co-author Omar Kudovic, my dear…